Which of the Following Best Describes the Threat Modeling Process
Iterative best describes the threat modeling process. Done right threat modeling provides a clear line of sight across a project that justifies security efforts.

Threat Modeling 12 Available Methods
Threat intelligence asset identification mitigation capabilities risk assessment and threat mapping.

. Threat modeling is a key responsibility for any cybersecurity team that is looking to protect their organization and their organizations assets. Which of among the following methodology distinguishes the security concerns of development from those of the infrastructure. Create an application overview.
The threat modeling process is iterative. Attack Which of the following issues can be addressed using an efficient logging system. Mitigation steps for each threat.
It takes inputs and generates outputs for each step in the process. A typical threat modeling process includes five steps. A mantrap is a small space with two separate sets of interlocking doors.
However threat modeling continues to. False A requirements model is the foundation of the _____ methodology. Threat Modeling Interview Question-Answer.
Penetration testing falls under which all-encompassing team Heather is performing a. Microsofts process of threat modeling can be utilized to do the process of threat risk modeling which performs below important tasks. Upon completion of the threat model security subject matter experts develop a detailed analysis of the identified threats.
Correct Answer is b Iterative. A security analyst for a large financial institution is creating a threat model for a specific threat actor that is likely targeting an organizations financial assets. 1Fixed 2Iterative 3Seldom refined 4Deterministic.
It is better to perform threat modeling from the. _____ generates a map that illustrates how the user moves through various features of the application. View-29960 Question Posted on 20 Jul 2020.
Identifying threats and vulnerabilities. 1Process Flow Diagram 2Sequence Diagram 3Data Flow Diagram 4Entity Diagram. It is better to perform threat modeling from the early stages of the SDLC.
The iterative threat modeling process. The process of identifying assets and threats in an organization is known as _____. The Process for Attack Simulation and Threat Analysis PASTA is a seven-step risk-centric methodology.
Which of the following best describes the threat modeling process. Which of the following best describes a mantrap. The purpose is to provide a dynamic threat identification enumeration and scoring process.
Its designed to help cybersecurity teams proactively find and identify potential risks and threats working through scenarios response models and other forms of threat detection. Including how severe a threat is and how much damage it could do. Trike Which of the following are the advantages of.
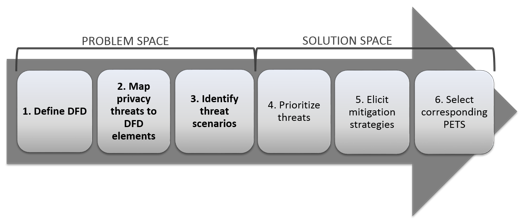
AIdentify threats b Provide countermeasures c Stop threats from happening Real Time d Help in flawless coding asked Mar 17 2021 in Threat Modeling by sharadyadav1986. Threat modeling helps to identify the security requirements of a system or process -- anything that is mission-critical processing sensitive or. The five major threat modeling steps are shown in Figure 1.
Start studying the Cybersecurity Chapter 2 Test flashcards containing study terms like Penetration testing is the practice of finding vulnerabilities and risks with the purpose of securing a computer or network. Threat modeling is a method of optimizing network security by locating vulnerabilities identifying objectives and developing countermeasures to either prevent or mitigate the effects of cyber-attacks against the system. By identifying and rating these security threats.
Clear objectives help you to focus the threat modeling activity and determine how much effort to spend on subsequent steps. Analysis of actions taken. It outlines the possible attacks that could be made on your applicationsystem.
Threat Modeling process can. Which of the following BEST describes the process by which code is developed tested and deployed in small batches. View-21182 Question Posted on 08 Jul 2020.
Threat modeling is a procedure for optimizing application system or business process security by identifying objectives and vulnerabilities and then defining countermeasures to prevent or mitigate the effects of threats to the system. Surveying or over-viewing of the application. Analysis of actions taken.
The threat model allows security decisions to be made rationally with all the information on the table. A requirements model is the foundation of the _____ methodology. A structured formal process for threat modeling of an application is described in Threat Modeling Process.
Q1 The following is a part of a threat model except _________. Threat modeling is a structured process through which IT pros can identify potential security threats and vulnerabilities quantify the seriousness of each and prioritize techniques to mitigate. Identifying the security objectives.
Application Threat Models DFDs can be used to determine the timingsequencing of the processes. Answered Mar 17 2021 by sharadyadav1986. Memorize flashcards and build a practice test to quiz yourself before your exam.
Repudiation Process Flow Diagrams are used by _____. A list of potential threats. A manager working in ABC Consulting shared a list of employees from his team who were eligible for an extra week off.
Which of the following best describes the threat modeling process. Which of the following best describes the threat modeling process. Which of the following security property does Spoofing violate.
The output of the threat modeling process is a _____ which details out the threats and mitigation steps. Threat modeling is a computer security optimization process that allows for a structured approach while properly identifying and addressing system threats. Each of these provides different insights and visibility into your security posture.
The process involves systematically identifying security threats and rating them according to severity and level of occurrence probability. Which of the following best describes the threat modeling process.

Model Of The Elements Of Strategic Management

Swot Analysis Swot Analysis Swot Analysis Template Swot Analysis Examples

Cybersecurity Maturity Model Cyber Security Device Management Maturity

Governance Risk And Compliance Grc Framework White Papers Metricstream Risk Management Strategies Risk Management Compliance

Devize For Cloud Based Monte Carlo Simulation In 2021 Reviews Features Pricing Comparison Pat Research B2b Reviews Buying Guides Best Practices Cloud Based Predictive Analytics Standard Deviation

Marketing Theories In A Nutshell Fourweekmba Portfolio Management P S Of Marketing Customer Experience Mapping

Pin On Cbt Worksheets From Psychology Tools

Threat Modeling 12 Available Methods

Tracing The Rainbow Through The Rain Learning To Ride The Emotional Waves Dialectical Behavior Therapy Dbt Skills Dbt Mindfulness

What Is The Tows Matrix And How To Use It Fourweekmba Swot Analysis Pestel Analysis Eisenhower Matrix

What Is The Tows Matrix And How To Use It Fourweekmba Swot Analysis Pestel Analysis Eisenhower Matrix

Porter S Generic Strategies Porter S Generic Strategies Leadership Strategies Strategies

Humans Are Visual Thinkers Images Photos Videos In Social Media Grabs Attention Explains Tough Concepts Inspire H Social Media Visual Content Tough

Organizational Silos Primer Https Flevy Com Browse Flevypro Doc 3842 Despite The Emergence Of Organizational Design Change Management Corporate Communication

Planning Security For Microsoft Dynamics Ax Ax 2012 Microsoft Dynamics Microsoft Topology

Scenario Planning Powerpoint Strategic Planning Strategic Planning Process Scenarios

Cybersecurity Reference Strategies Linkedin Cyber Security Enterprise Architecture Microsoft Ignite
Threat Modeling 12 Available Methods

Cybersecurity Reference Architecture Security For A Hybrid Enterprise Microsoft Security Blog Enterprise Architecture Cyber Security Security Architecture
Comments
Post a Comment